RAVID Framework
Randomized Adaptive Virtual Infrastructure Defense (RAVID) is the core architecture behind ENIGMA's stealth networking.
It advances the Adaptive Moving Target Defense (AMTD) model by introducing continuous transformation at the infrastructure level.
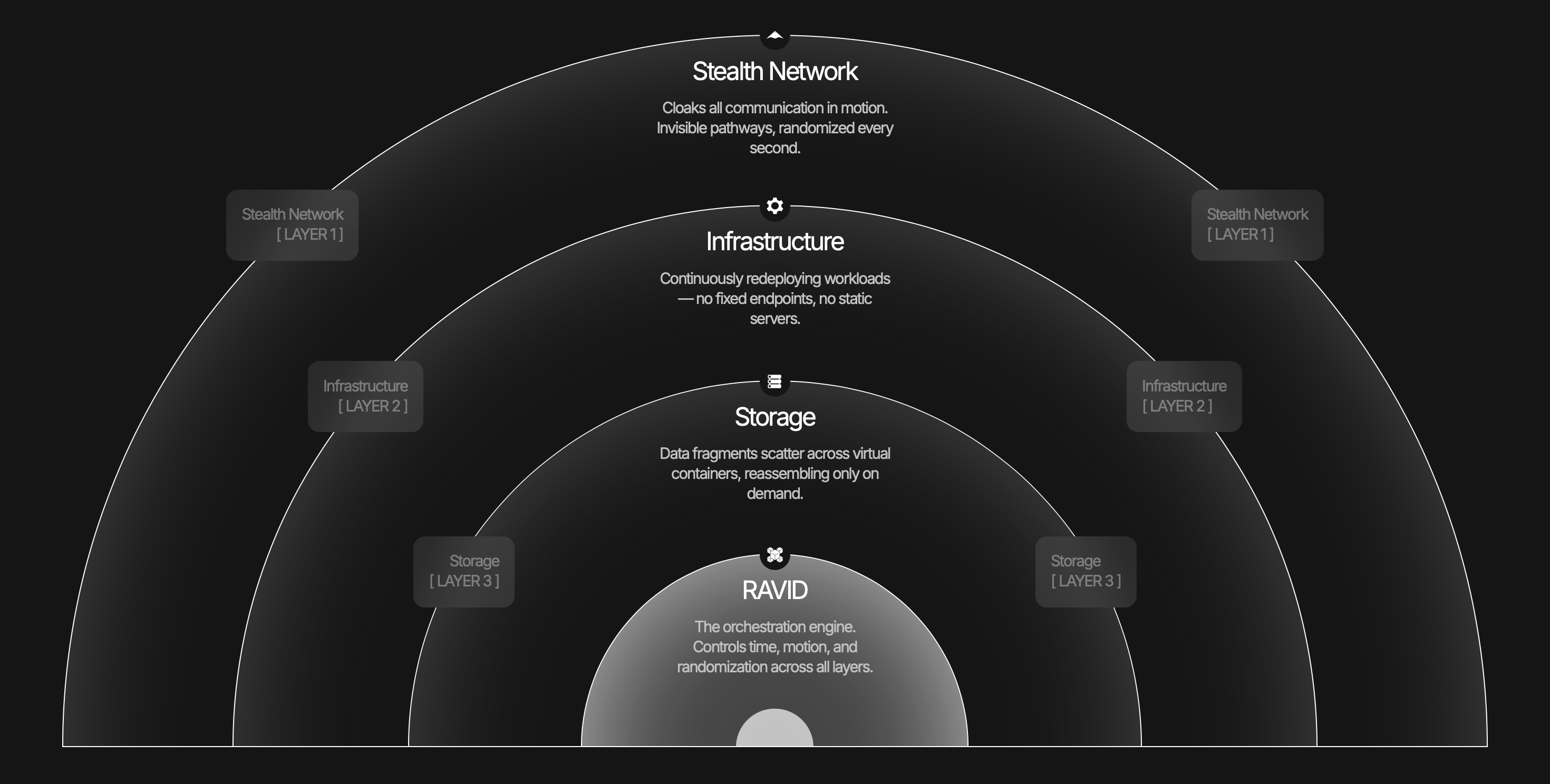
What RAVID Does
RAVID eliminates the reconnaissance phase of cyberattacks by removing what attackers look for:
- Randomized and Abstracted Identities - Service identities change continuously
- Ephemeral Service Instantiation - Resources exist only when needed, then vanish
- Moving Target Authorization - Access points shift unpredictably
The result: infrastructure that can't be mapped, flows that can't be analyzed, and services that don't exist until the exact moment an authorized identity requests them.
RAVID prevents quantum AI reconnaissance and hides all service existence.
Breaking the Kill Chain
Traditional defenses try to stop attacks in progress. RAVID prevents them from starting.
| Attack Stage | Traditional Defense | RAVID Response |
|---|---|---|
| Reconnaissance | Firewall, IDS | No endpoints to scan |
| Weaponization | Threat intel | No service visibility to target |
| Delivery | Email filters, AV | Unauthenticated traffic dropped |
| Exploitation | Patching, WAF | Ephemeral services - no stable target |
| Installation | EDR, sandboxing | No exploitation = no persistence |
| C2 | Traffic monitoring | Identity-only traffic - C2 impossible |
| Exfiltration | DLP, monitoring | No access = no data movement |
RAVID doesn't engage with attacks. It makes the infrastructure non-existent from an adversary's perspective.
The Metadata Problem
Modern surveillance and attacks rely on metadata - timing, routing, packet sizes, flow patterns.
Even encrypted traffic leaks these signals. AI can model them. Quantum compute will eventually break the encryption.
RAVID removes the signal entirely:
- No flows to intercept
- No patterns to analyze
- No probability space for quantum inference
Built on OpenZiti
RAVID leverages OpenZiti's zero trust architecture:
- No public-facing application surfaces
- Mutual TLS authentication for all connections
- Identity-native routing
- Fully cloaked traffic
The network becomes the defensive perimeter. Everything outside it sees nothing.
Quantum-Ready by Default
Instead of racing to build quantum-resistant encryption, RAVID makes the problem irrelevant.
With no exposed services, no collectible flows, and no persistent identities, there's nothing for quantum-enabled attackers to target - regardless of computational power.
The Network as Defense
In RAVID architecture, the network is no longer an attack vector.
It provides a cloaking effect to the infrastructure, making it the first line of defense. Web applications, cloud resources, and on-premise systems all benefit from this invisibility layer.
The infrastructure doesn't fight attacks. It simply isn't there to be attacked.
They can't map what doesn't stay still. They can't attack what they can't find.