What is ENIGMA?
ENIGMA is a security architecture built on the RAVID framework that makes infrastructure invisible and continuously adaptive.
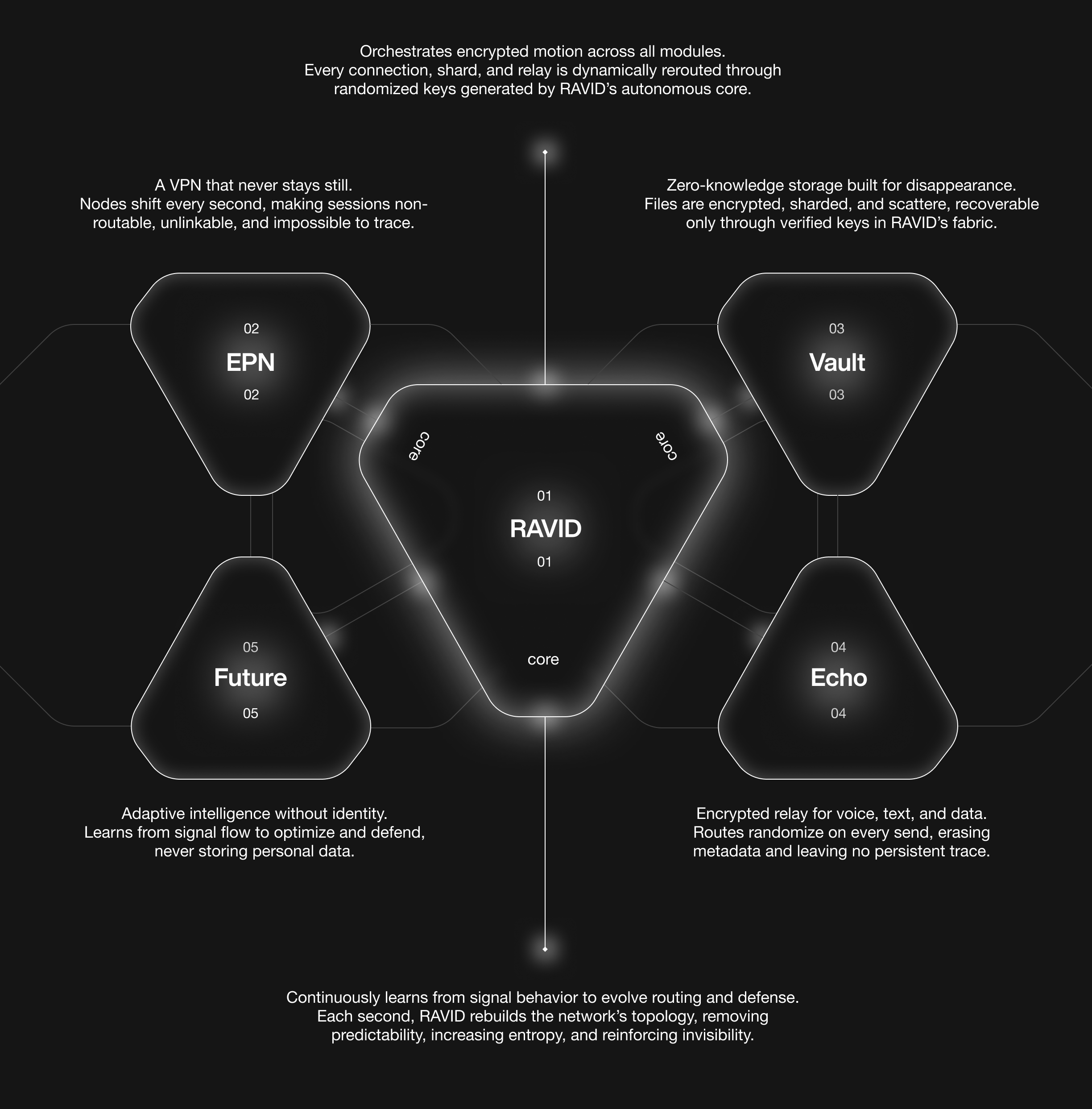
How It Works
Invisible Infrastructure
Networks and applications are non-routable from any external location. There's no attack surface to discover.
- No ports to scan
- No DNS records to enumerate
- No predictable addressing
- No reconnaissance surface
Authorization happens through identity verification, not network location.
Continuous Transformation
Infrastructure components exist temporarily, change constantly, and provide no persistent target.
- Resources instantiate on-demand
- Network topology reconfigures dynamically
- Service identities rotate
- Paths and endpoints shift unpredictably
Attackers can't develop reliable attack patterns against infrastructure that refuses to stay still.
Zero Metadata Design
Traffic flows are invisible. No patterns to collect, no timing to analyze, no metadata to store for future decryption.
Built on OpenZiti's zero trust architecture with identity-native routing and mutual TLS everywhere.
The Difference
Traditional: Detect and respond to attacks on exposed infrastructure
ENIGMA: Remove the infrastructure from adversary visibility entirely
Attackers need reconnaissance to succeed. ENIGMA makes reconnaissance impossible.
Built For
- Enterprises operating critical infrastructure
- Organizations handling sensitive data
- Applications requiring stealth operation
- Any system where exposure equals risk
ENIGMA works with existing infrastructure. Deploy zero trust networking without replacing current systems.